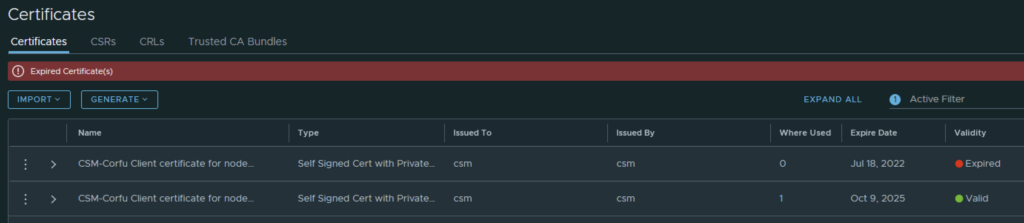
Enabling SSH on NSX appliances via the CLI (Command Line Interface) is an essential skill for VMware administrators, providing a more direct and scriptable approach to managing and configuring the NSX environment. Here’s how to enable SSH on NSX from the CLI, allowing for secure, remote administration of your virtual network infrastructure.
Pre-Requisites
Ensure you have local or console access to the NSX appliance (NSX Manager, NSX Edge, or Controller) for initial setup. Administrative credentials will be required to execute the following commands. The instructions have been tested on NSX 4.1.2.3
Steps to Enable SSH on NSX via CLI
- Access the NSX Appliance CLI: Connect to the console of the NSX appliance.
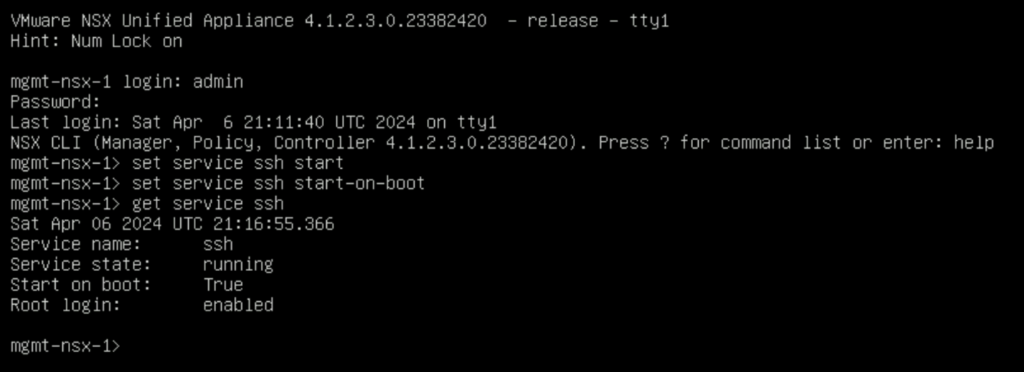
- Log in as Admin: Use the username
adminand the password configured during the NSX appliance setup to log in. - Enable SSH Service: Execute the command
set service ssh startto enable the SSH service. This command starts the SSH daemon, allowing SSH connections to the appliance. - (Optional) Configure SSH Service to Start on Boot: To ensure the SSH service is automatically started upon system reboot, execute
set service ssh start-on-boot. This step is crucial for maintaining remote access after system restarts. - Verify SSH Service Status: To confirm the SSH service is running, you can use the command
get service ssh. This command displays the current status of the SSH service, including whether it’s running and if it’s configured to start on boot.
Security Considerations
When enabling SSH, consider implementing security measures to protect your NSX environment:
- Use Strong Passwords: Ensure that all user accounts have strong, complex passwords.
- Implement Access Control: Restrict SSH access to trusted hosts or networks using firewall rules.
- SSH Key Authentication: For enhanced security, use SSH key-based authentication instead of passwords.
- Regularly Update and Patch: Keep your NSX and all connected systems up to date with the latest security patches.
Conclusion
Enabling SSH on NSX via the CLI is a straightforward process that enhances the manageability and accessibility of your network virtualization environment. With SSH enabled, administrators can securely manage the NSX appliances from remote locations, streamlining operations and maintenance tasks. Always follow security best practices to safeguard your environment against unauthorized access.