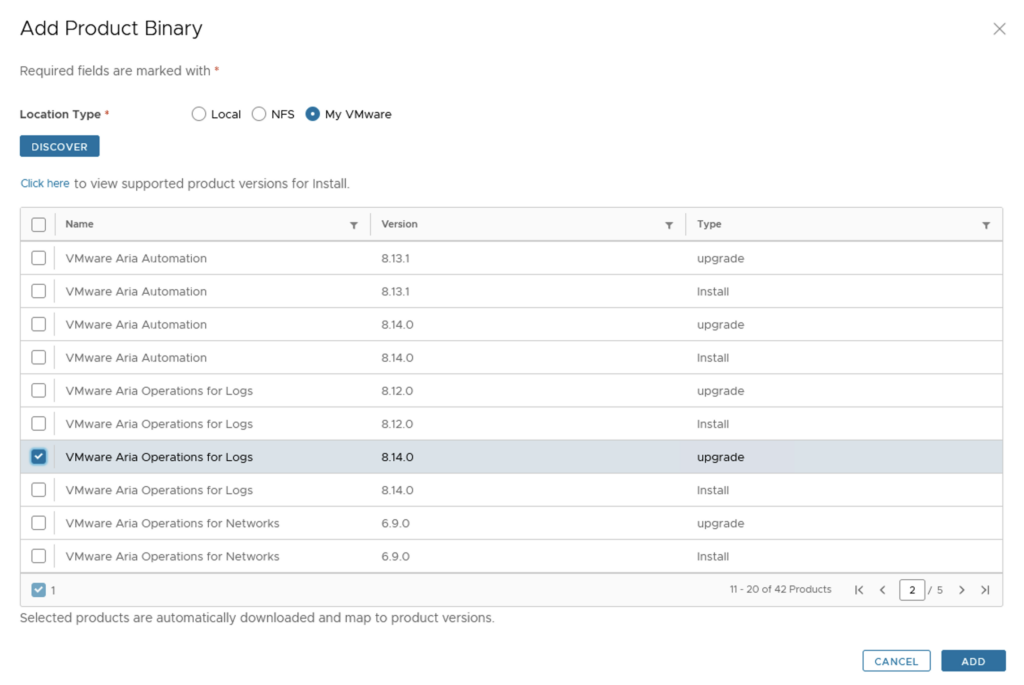
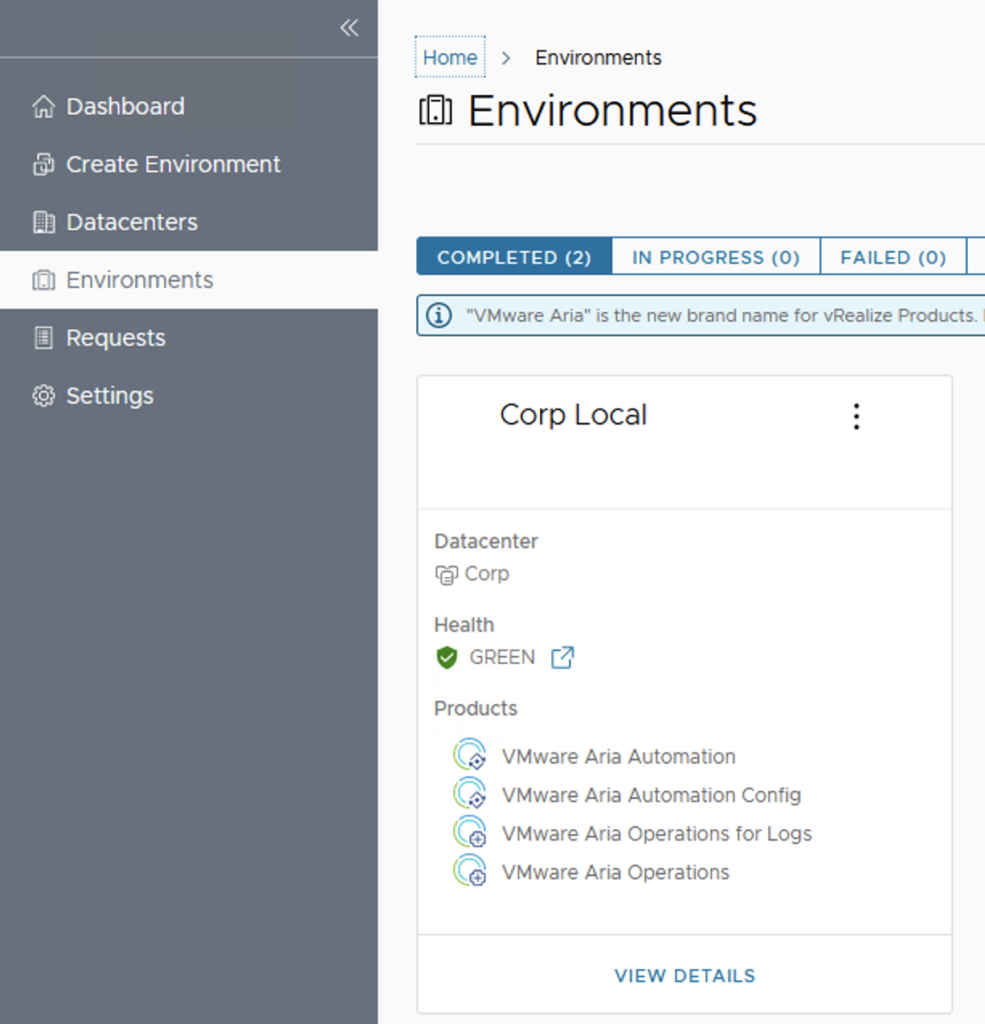
Introduction
When it comes to deploying a three-tier application in Google Cloud Platform (GCP), there are several tools available, including vRealize Automation (vRA) 8, Terraform, and Ansible. Each tool has its own strengths and weaknesses, and choosing the right one for your project depends on several factors. In this blog post, we will compare these three tools and discuss how vRA 8 stands out as the best option for deploying a three-tier application in GCP.
Overview of vRA 8, Terraform, and Ansible
vRealize Automation (vRA) 8 is an enterprise-grade cloud automation and management platform that allows you to automate the deployment and management of complex applications and infrastructure. It provides a wide range of tools and services that can be used to deploy and run applications in the cloud, including GCP.
Terraform is an open-source infrastructure as code (IaC) tool that allows you to define, deploy, and manage infrastructure in a consistent and repeatable way. It uses a simple, declarative language for defining infrastructure and supports many cloud providers, including GCP.
Ansible is an open-source automation tool that allows you to automate configuration management, application deployment, and task automation. It uses a simple, human-readable YAML syntax for defining tasks and supports many cloud providers, including GCP.
Comparison of vRA 8, Terraform, and Ansible
When it comes to deploying a three-tier application in GCP, each tool has its own strengths and weaknesses. Let’s take a look at how vRA 8, Terraform, and Ansible compare.
Ease of Use
vRA 8 is an enterprise-grade platform that provides a user-friendly interface for deploying and managing infrastructure and applications. It has a drag-and-drop interface for creating blueprints, which makes it easy to create and manage complex applications. It also provides a centralized platform for managing infrastructure, which can be useful for large organizations with many teams.
Terraform is a powerful IaC tool that requires some knowledge of infrastructure and coding. It uses a declarative language for defining infrastructure, which can take some time to learn. However, once you understand the syntax, it can be very powerful and flexible.
Ansible is a simple and easy-to-use automation tool that uses a human-readable YAML syntax for defining tasks. It does not require any coding knowledge and can be learned quickly by IT operations teams.
Scalability
vRA 8 is designed to handle large-scale deployments and provides many tools for managing infrastructure at scale. It can handle complex application deployments and can scale to meet the needs of large organizations.
Terraform is also designed to handle large-scale deployments and provides many tools for managing infrastructure at scale. It can handle complex application deployments and can scale to meet the needs of large organizations.
Ansible is not designed for large-scale deployments and can be difficult to scale for large organizations. However, it is a good option for small to medium-sized organizations that need to automate simple tasks.
Flexibility
vRA 8 is a very flexible platform that provides many tools and services for deploying and managing infrastructure and applications. It can integrate with many other tools and services, which makes it a good option for complex environments.
Terraform is also a very flexible tool that provides many options for defining infrastructure. It supports many cloud providers and can be used to deploy complex applications.
Ansible is a flexible tool that can be used for many different tasks, including configuration management, application deployment, and task automation. It supports many cloud providers and can be used to automate many different tasks.
Cost
vRA 8 is an enterprise-grade platform that requires a license and can be expensive for small organizations.
Terraform is an open-source tool that is free to use
Ansible is also an open-source tool that is free to use.
Why vRA 8 stands out for deploying a three-tier application in GCP While Terraform and Ansible are both great tools for deploying infrastructure, vRA 8 stands out for deploying a three-tier application in GCP for several reasons.
Firstly, vRA 8 is a powerful platform that provides a user-friendly interface for creating blueprints and managing infrastructure. It is designed to handle large-scale deployments and provides many tools for managing infrastructure at scale.
Secondly, vRA 8 provides many integration options with other tools and services, which makes it a good option for complex environments. It can integrate with many different cloud providers, including GCP, and can be used to automate complex application deployments.
Finally, vRA 8 provides many advanced features, such as self-service provisioning, policy-based governance, and cloud cost management, which makes it a good option for enterprise-grade applications.
Conclusion
When it comes to deploying a three-tier application in GCP, vRealize Automation (vRA) 8, Terraform, and Ansible are all good options. Each tool has its own strengths and weaknesses, and the best choice for your project depends on several factors. While Terraform and Ansible are both great tools for deploying infrastructure, vRA 8 stands out as the best option for deploying a three-tier application in GCP due to its powerful platform, user-friendly interface, and advanced features.